FREE Cyber Security Risk Assessment for your business
Protecting you from Cyber Crime, your privacy is our priority
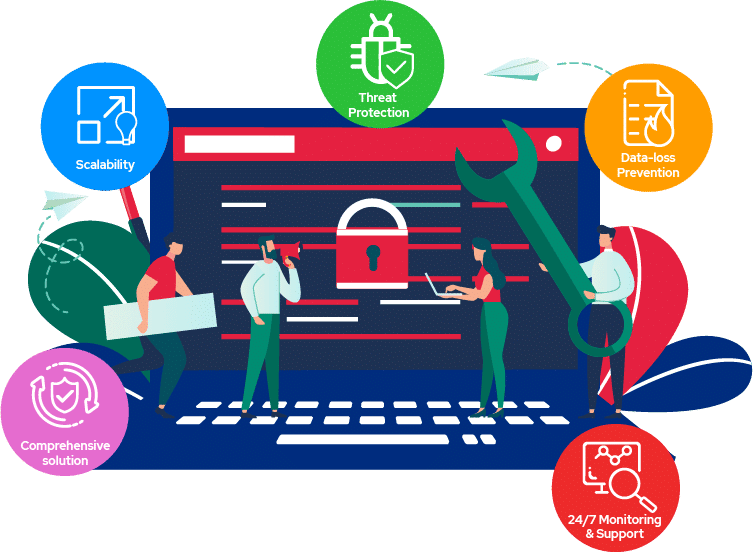
Fast scalable, managed cyber security that offers end-to-end comprehensive protection. Tailored cyber security for global data loss prevention and automated threat protection.
Featured Cyber Security Services
Strategy
Cyber security strategy to eliminate vulnerabilities.

Cyber threat intelligence
Accurate and relevant cybercrime intelligence.
Cyber risk management
Minimize, monitor and control cyber threats.
Network security
Network protection and monitoring solution.

Mobile security
Protecting portable devices for end users.

Content and data
Digital certificates and email monitoring solution.
Threat Protection
Uncover and terminate any suspicious activity

Data-loss Prevention
Preventing any loss or damage to your data

Scalable Solutions
Safeguard your business of any size against threats

Tailored Solution
Robust solutions designed to meet your business needs
Explore our Cyber Security Benefits
Gain a competitive advantage with trusted cyber security

Threat Protection
Our solutions gives your business the ability to uncover and terminate any suspicious activity that attempts to jeopardize your business.

Data-loss Prevention
Security solutions that monitor and manage your data to prevent any loss or damage.

Scalability
Complete business protection that safeguards your business from cyberattacks and data-loss.

Tailored Solutions
Robust solutions are tailored to each individual business to enhance our protection capabilities.

Managed Operations
Our solutions gives your business the ability to uncover and terminate any suspicious activity that attempts to jeopardize your business.

Automated Upgrades
Cybersecurity solution that is constantly upgrade to offer robust threat prevention against any new or old forms of cyberattacks.

Comprehensive Solution
Empowering your business with cybersecurity that grows as your business grows, protect your entire business no matter the size.

24/7 Monitoring and Support
Our solutions includes extended monitoring to ensure your business is always protected against cyber security threats.
Explore our Cyber Security Services
Give your business the advantage of Secured Enterprise
Network Security
Our managed solution empowers your business as we monitor your network to ensure that any threats are detected and eliminated.
Digital Security
Reliable cybersecurity that protects your online identity. Safeguard your business with a security solution that identifies and protects your assets.

Mobile Security
Safeguard your portable devices with a mobile security solution that does not affect the general user experience.

Managed Operations
Our solutions gives your business the ability to uncover and terminate any suspicious activity that attempts to jeopardize your business.
Automated Upgrades
Cybersecurity solution that is constantly upgrade to offer robust threat prevention against any new or old forms of cyberattacks.

Comprehensive Solution
Empowering your business with cybersecurity that grows as your business grows, protect your entire business no matter the size.
Who We Are
Secured Enterprise is a certified global online cyber security leader. Our company was established due to the growing need for organizations to focus on cyber threats around cloud security, mobile and network security.
With the rise of cyber security threats coming from everywhere and at any time, Secured Enterprise understands the importance of securing your network from threats 24/7. We have a proven track record in helping large organizations manage their security network by protecting, monitoring and analyzing data with a wide range of physical, network and virtual IT Infrastructure in real-time.
At Secured Enterprise, we understand that cyber security is about managing risk, but it is equally about enabling organizations to take advantage of opportunities in today’s digital world, in a safe way, while maintaining the trust of their customers.
With the rise of cyber security threats coming from everywhere and at any time, Secured Enterprise understands the importance of securing your network from threats 24/7. We have a proven track record in helping large organizations manage their security network by protecting, monitoring and analyzing data with a wide range of physical, network and virtual IT Infrastructure in real-time.
At Secured Enterprise, we understand that cyber security is about managing risk, but it is equally about enabling organizations to take advantage of opportunities in today’s digital world, in a safe way, while maintaining the trust of their customers.
Our Methodology is simple and effective. It has evolved into an action plan that is linked to a secure cloud management methodology. Our experience has taught us that while the internet continues to evolve into a mesh of cloud environments (privately owned, public or hybrid) the fundamental objectives for organizations today is to maintain secure environments in an increasingly globalized world.
No organization or government can ever predict or prevent all (or even most) attacks; but they can reduce their attractiveness as a target, increase their resilience, and limit damage from any given attack.
Learning how to stay ahead is challenging and takes time, but the benefits for the organization are considerable. The organization will be able to exploit the opportunities offered by the digital world, while minimizing exposure to risks and the cost of dealing with them.
No organization or government can ever predict or prevent all (or even most) attacks; but they can reduce their attractiveness as a target, increase their resilience, and limit damage from any given attack.
Learning how to stay ahead is challenging and takes time, but the benefits for the organization are considerable. The organization will be able to exploit the opportunities offered by the digital world, while minimizing exposure to risks and the cost of dealing with them.
Explore our Expert Cyber Solutions
Effective and efficient Cyber Security with extended monitoring
to identify, report and respond to security threats.
to identify, report and respond to security threats.
Strategy
By analyzing your company’s security
defences, we establish the vulnerabilities
that your company might have and create
a tailored security solution that fills the
gaps and the needs for your business.
Cyber Threat Intelligence
Threat Intelligence, is organized, analyzed
and refined information about potential or
current attacks that threaten an organization.
The initial purpose of threat intelligence is to
help a company understand the risks.
Mobile Security
The next step in securing your business is to
have a risk management plan in place to
minimize, monitor and control the impact that
the risks might have on your business.
Latest News

Cybersecurity, A Central Issue For All Organizations
“Companies lacking a clear approach to cybersecurity are at a considerable disadvantage and less likely to survive in today’s highly competitive world”

How We Can Protect You From Ransomware
Phishing is a type of cybercrime used to steal personal data from unsuspecting people. This personal data is usually very sensitive. In most cases, the fraudulent attempt is usually to acquire information such as…

Data Breach In IT With Digital Security
Data breach is an incident that involves the unauthorized or illegal viewing, access or retrieval of data by an individual, application or service. It is a type of security breach specifically designed to steal and/or publish data to an unsecured or illegal location.
Supported Technologies










Copyright © Secured Enterprise | Designed by eNew Media
